Microsoft Defender for Office 365
Microsoft Defender for Office 365 should be considered a core security tool for any organisation as it links the Online protection of Office 365 emails (called EOP – Exchange Online Protection) with the files and folders that are used as part of the Office 365 licensing such as SharePoint, OneDrive folders on a corporate network.
Let’s remind ourselves of these groups, and highlight the group this guide addresses:
- Protection at the endpoint level.
- Delivered via a unified platform for both preventative protection, detection as well as automated investigated and response.
- Protection at the email level and collaboration tools.
- Safeguarding measures against malicious threats via email messages, links and other collaboration tools.
- Protection at the identity level via Azure Active Directory Domain Services (Azure AD DS).
- Identify / Detect / Investigate compromised identities and insider actions.
- Previously known as Microsoft Advanced Threat Protection (ATP)
- Protection at the Application level.
- Cross SaaS based solution allowing deep visibility, data controls and threat protection across business aps.
Many users believe mistakenly that the Exchange Online Protection functionality in many of the standard Microsoft Office products will protect them from antivirus, phishing and attacks based outside the email system, which is why this guide has been created and why the new Microsoft security tools have been reorganised to make the levels of protection and functionality clearer to understand.
The Microsoft Defender for Office 365 incorporates the Exchange protection functionality and builds on this to provide users with a comprehensive set of security measures that can be tailored to match the exact user behaviours within an organisation helping to provide proactive threat protection for your organisation. It comes with two plan options Microsoft Defender for Office plan 1 or 2, we will discuss both.
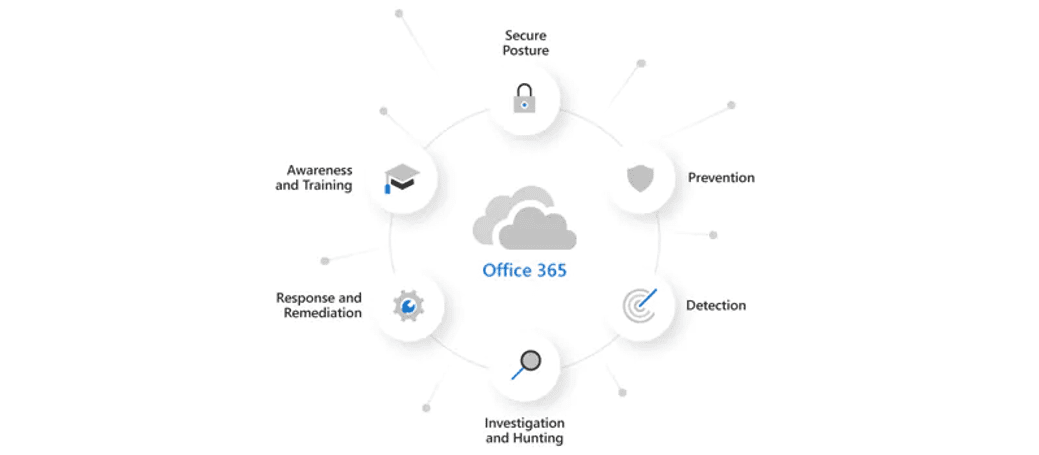

Microsoft Defender for Office 365 Plan 1 (MDO P1) is geared to be a defensive tool, with its main function being the protection and detection of cyber threats. The work required to get these protections in place is the development of rules and processes that can be applied to a user community based on the individual or group risks to the business. Usually, this will need an experienced security expert to assess the best methods and rules to develop.
Microsoft Defender for Office 365 Plan 2 (MDO P2) moves the security stance from a reactive protection and defence stance to a proactive investigate and respond stance as shown in the diagram.
The features of the Plan 2 are even more geared to a security professional and therefore most organisations seek assistance from a provider like Vissensa who can develop the processes around managing and monitoring an organisation’s cyber security.
To decide which plan is right for an organisation, let’s break down the features in each plan and their use.
Microsoft Defender for Office 365 Plan 1 vs Plan 2 – Which license is the most suitable?
Microsoft Defender for Office 365 Plan 1
As mentioned earlier, if you subscribe to Microsoft Defender for Office 365 plan 1 you will automatically get all of the functionality of Microsoft Exchange Online protection (EOP) which is included with a Microsoft 365 subscription.
To recap these features protect users Online email accounts from antispam, phish and malware, bulk email, spoofing of users, and email impersonation. The tool comes with the ability to quarantine emails and allow/block URL’s and files contained in email traffic.
Plan 1 takes these features and adds the protection to elements of a system that users will access to collaborate with each other, such as accessing SharePoint sites, OneDrive accounts and files and folders on corporate networks.
Specifically, the Plan 1 subscription provides:
Safe attachments
Controlled by a safe attachment policy written to cover specific users, groups or domains by your security team, Safe Attachments provide greater protection for email attachments that have already been scanned by the Exchange Online Protection (EOP) function by making additional checks on the attachments in a self-contained space away from the user before being delivered to the recipients.
Safe links
Protecting users from inadvertently clicking on links and URLs that have been specifically designed to attack a user or organisation is critical as it forms the most common successful example of an attack vector that hackers use.
Safe Links is specifically focused on intercepting these links and URL’s and actively scanning and creating ringfenced areas that open, interrogate, rewrite and scan these links using sensors to capture the behaviour of the link and to catalogue if the attack is known or unknown. If suspicious, then it is quarantined and the user is prevented from opening, if it is legitimate, it is passed through the normal mail flow to the recipient.
Safe Links protection applies to email links and URL’s in a preset security policy in the EOP product and can be applied to at the user, group of users (department) or domain levels.
In addition Safe Links protection is available for links shared in Teams collaboration and conversations, group chats, or from corporate channels are also controlled by Safe Links policies.
Safe Attachments for SharePoint, One Drive and Microsoft Teams
Using the asynchronous common virus detection engine in Microsoft 365, Safe Attachments for SharePoint, OneDrive, and Microsoft Teams in Microsoft Defender for Office 365 provides an additional layer of protection for users collaborating in these environments. This feature helps detect and block existing files that are identified as malicious in team sites and document libraries within a corporate network, preventing the inadvertent spread of malware and viruses by corporate teams or individual users collaborating with each other.
When Safe Attachments for SharePoint, OneDrive, and Microsoft Teams is enabled and identifies a file as malicious, the file is locked using direct integration with the file stores and flagged to the user as shown below.
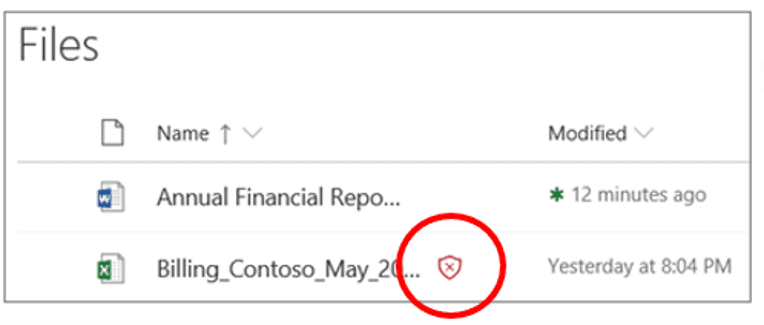

Defender for Office 365 will not scan every single file in SharePoint Online, OneDrive for Business, or Microsoft Teams. This is by design. Files are scanned asynchronously. The process uses sharing and guest activity events along with smart heuristics and threat signals to identify malicious files. Note that the visual flags for users (shown in the example above) can only be used if SharePoint has been configured to use the Modern Experience.
Anti-phishing
Anti phishing includes the impersonation of sender or the sender’s email domain in a message looks similar to a real sender or domain:
Microsoft Defender for Office 365 protects against specified internal or external email addresses from being impersonated as message senders such as a user receiving a message from the finance director to confirm the bank account details of the company. Many users wouldn’t question the request from a senior executive so this feature protects users from being impersonated.
When you add internal or external email addresses to the Users protect list, messages from those senders are subject to impersonation protection checks. If impersonation is detected in the sender’s email address, the impersonation protection actions for users are applied to the message (what to do with the message, whether to show impersonated users safety tips, etc.).
This feature also enables domains to be protected by creating a policy that lists the sender domains that are to be protected from impersonation.
Threat Explorer and Real time detection
Explorer or Real-time detections helps your security operations team investigate and respond to threats efficiently using a wide range of reports and analysis that can be viewed historically or in real time.
This feature is specifically geared to security experts who can quickly interpret and analyse the data being provided to fine tune an organisations security policies and procedures.
Threat explorer and real time detection operates with the Microsoft Security & Compliance Center, where Threat management, Explorer or Real-time detections are options.
Microsoft Defender for Office Plan 2
Microsoft Defender for Office 365 Plan 2 expands the capabilities of the security team’s ability to become more proactive against cyber threats by increasing the investigation and response functions available to them and adding the ability to ability to go on the offensive and hunt down potential threats with aid of automated tooling called Threat Explorer.
As described earlier these tools are specifically designed to be used by security experts who can run, interpret and act on the results for the Microsoft Security & Compliance Centre dashboard. Vissensa as an MSP with years of secure operations can assist in the design, development and ongoing management of an organisation’s security posture.
The key elements of Plan 2 are:
Threat Trackers
Threat Trackers are widgets and views that provide intelligence on different cybersecurity issues that have been identified as potentially impacting your organisation, such as trending malware that is being tracked.
Using a feature called Noteworthy trackers, a company can stay informed by the cyber security community on known and rising cyber threats that might impact an organsiation and provide the security team with intelligence about how and where to defeat the threat before it gets to your network.
Through the features of tracked and saved queries, a longer historical view of where and how threats have presented themselves to your organisation’s network and afford the security team to harden specific systems and educate specific users that are highlighted as suing poor security practices.
Threat Explorer and Real time detection
Explorer or Real-time detections helps your security operations team investigate and respond to threats efficiently using a wide range of reports and analysis that can be viewed historically or in real time.
This feature is specifically geared to security experts who can quickly interpret and analyse the data being provided to fine tune a organisations security policies and procedures.
Threat explorer and real time detection operate with the Microsoft Security & Compliance Center, where Threat management, Explorer or Real-time detections are options.
Automated investigation and response (AIR)
Automated investigation and response (AIR) provides a tool that can assist your security team to focus on tasks that utilise their expertise while automating some of the known and repeatable actions required to keep a corporate network and user community safe.
Automating some of the security tasks particularly those of volume during busy periods and triggering an alert to the team when detecting a suspicious email, file or URL allows the prioritisation and response to those alerts at the right point.
Once a suspicious email or URL is identified, (AIR) collects information about how and what suspicious content is, what the attack is focused on and if other assets are affected while in real time reporting the outcomes and results to the team and initiating remediation actions against the threat.
Microsoft 365 provides many built-in alert policies that help identify Exchange administrator permissions abuse, malware activity, potential external and internal threats, and information governance risks. Several of the default alert policies can trigger automated investigations.
Simulated Phishing Attacks
The ultimate in cyber defence is the ability to test how well an organisation’s cyber security posture is using real attacks without the consequences of an attack.
Attack simulation training will allow your experienced security team to run simulated cyber attacks against the defences that you currently have in place protecting your business. They are designed to stress test security policies and practices, exposing where air gaps are present and where attacks could succeed, giving valuable information to the security team to enhance the security of the systems.
It also acts as a valuable training tool that can be used to increase the awareness of employees to the cyber risks in an organisation, reducing the risk of them becoming a cyber victim and endangering the business.











