Microsoft Defender for Endpoint
Security tools are continuing to become smarter, and some might say that Microsoft’s responsibility to help end users and businesses is becoming more vital. The attack or threat vectors (how hackers can get to your systems and data) are becoming wider and to counter this, the Microsoft suite of security tools have been aligned into specific groups.
Let’s remind ourselves of these groups, and highlight the group this guide addresses:
- Protection at the endpoint level.
- Delivered via a unified platform for both preventative protection, detection as well as automated investigated and response.
- Protection at the email level and collaboration tools.
- Safeguarding measures against malicious threats via email messages, links and other collaboration tools.
- Protection at the identity level via Azure Active Directory Domain Services (Azure AD DS).
- Identify / Detect / Investigate compromised identities and insider actions.
- Previously known as Microsoft Advanced Threat Protection (ATP)
- Protection at the Application level.
- Cross SaaS based solution allowing deep visibility, data controls and threat protection across business aps.
Endpoints are the “edge” devices that are used to connect to a systems and data within a corporate network by its users. These devices range from mobile phones, tablets, laptops, browsers via public networks to other computer equipment and devices that can establish a connection to corporate systems.
Defender for Endpoints has been designed to provide security measures that can be applied to connected devices to prevent unauthorized access and infection by malware and viruses that would otherwise go undetected by the user and could transmit its payload to connected devices and systems.
Importantly, Endpoint which leverages an organisations Mobile Device Management (MDM) strategy, is significantly different to the email and file security products offered by Microsoft in terms of how it is installed and managed as a sensor or agent is required to be loaded to each device which then manages the capability of the device to connect as well as reports back the connection status and access requests to a central management hub which will automatically determine if the device is given access or not.
The sensors interrogate the device for information such as the current release and patch level and can deny access if this could compromise the network hence why a Mobile Device Management strategy implemented by an organisation can work in tandem with Defender for Endpoints by automating the patching of devices and determining the current patch and security status of a particular device managed under MDM. The user is also identified and metrics such as password and pin security can be managed to ensure that the device is as secure as possible. All these measures form part of the Microsoft Defender for Endpoint posture.
The Endpoint product comes with two plans, Plan 1 – which is focused on the user devices and Plan 2 which is geared to a proactive stance in fighting cyber security.

Microsoft Defender for Endpoint Plan 1 vs Plan 2 – Which license is the most suitable?
Microsoft Defender for Endpoint Plan 1
The Microsoft for Endpoint Plan 1 services provide the baseline security features under the Microsoft Defender product umbrella and in turn, sits around the reactive approach to actioning security concerns and threats at the device and user level. It augments the cyber security measures contained in the Exchange Online Protection product and the Microsoft Defender for Office 365 products which are focused on email, file and folder security.
With this plan the Systems Administrator or Security Team (SecOps) can manually invoke Antivirus scans, stop processes from running and quarantine the files on the device that look suspicious, block files and executables from access and isolate the device from the network if required.
Microsoft For Endpoint Plan 1 also guards against devices attempting to download and run files and scripts on the network, analysing obfuscated code and behaviours considered abnormal actions in users’ day to day access to the system. As a common ransomware tactic is to “lock” an organisation’s files and folders, Microsoft Defender for Endpoints also provides ransomware mitigation through controlling the access authority and actions available to users when using folders.
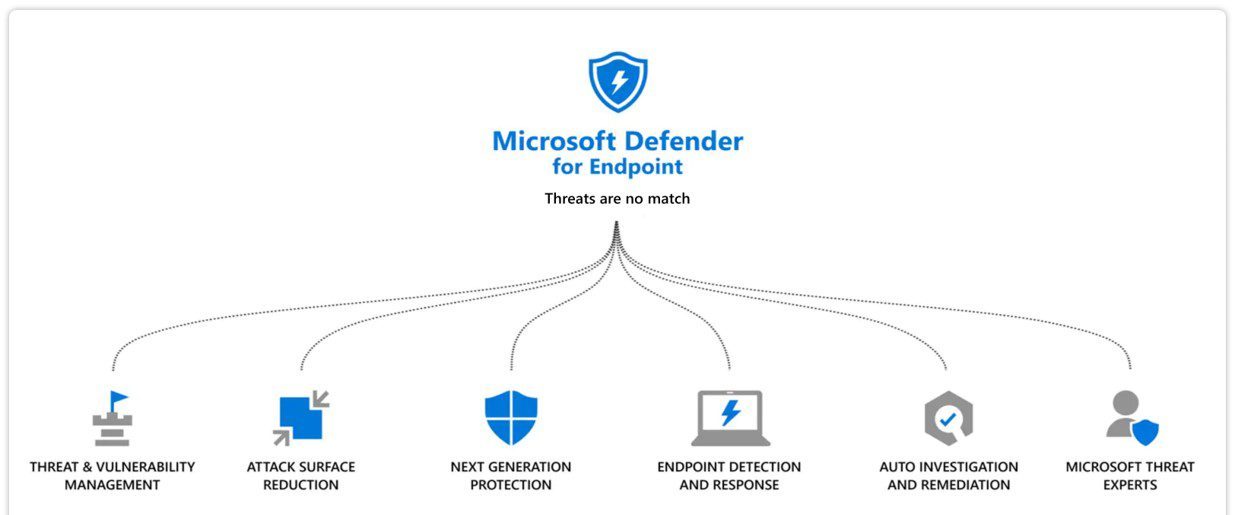
The specific features of Microsoft Defender for Endpoint Plan 1 are:
Next Generation Protection – covering antimalware and antivirus protection at all levels.
Attack Surface Reduction – Determining wherever your business may be vulnerable to attacks, and mitigation by reducing these surfaces of exposure. Covering rules, device control, web protection, network protection, firewall and application control.
Manual Response Actions – A set of pre planed actions that can be run by a security team on a device that has been attacked, such as running an AV scan, isolating a device from the network, quarantining or adding indicators on when to block/allow a file
Centralised Management – Singel pane of glass view accessibility through the Microsoft Defender Portal as part of the Microsoft stack.
Reporting – helps to provide easy access to information on detected threats and any actions that were taken to address these problems
Microsoft Defender for Endpoint Plan 2
Microsoft Defender For Endpoint Plan 2 services take a more proactive approach with automation, vulnerability management and hence has a cost increase compared to Microsoft Defender For EndPoint Plan 1. It also requires a more specialist approach to security management and lends itself to System Administrators or SecOps teams and companies such as Vissensa who can set up and manage such tools. The additional productivity to cyber security that comes with Plan 2 are:
Threat and Vulnerability Management
This feature is enabled to discover vulnerabilities on the devices and in the network on the fly through real time sensors. This proactive approach takes the fight to the attackers by actively developing the security stance required based on real time information rather than waiting for an attack and manually intervening with periodic threat scans. The tool significantly reduces operational exposure to threats alongside hardening endpoints or the threat surface that they can be exposed to.
Threat Hunting and Automation
By performing threat hunting, Defender will analyse the last 30 days of raw data and proactively inspect threats and behaviours learning how the systems and network are used and developing processes to help prevent both known and potential threats to your business. Adding this to the automation element ensures that should an attack succeed the right focus by the security team can be applied to the important tasks of mitigation rather than being distracted by constant alerts from potential as yet un launched risks.
Endpoint Detection and Response (EDR)
This feature takes cyber protection to the next stage by not only enabling tools that are proactive but also developing an “assume breach" mindset, by continuously collecting behavioural activity including process, network activities, memory, registry and file system changes and user activities at logon. Stored for six months, this information provides insight to how attacks were executed from different systems and user behaviours
Managed Threat Service via Microsoft Threat Experts
As part of the additional service under Microsoft Defender For Endpoints Plan 2, businesses can also take advantage of Microsoft Threat Expert notifications sent to inform the business of the most widespread threats affecting the organisation. Additionally, customers can engage with security experts directly from within Microsoft Defender Security Centre who can provide further insights needed to better understand the complex threats affecting your organisation.
Microsoft Defender for Endpoint vs Third Parties
At the time of writing this guide, Microsoft Defender for Endpoint is still a relatively new service to the Microsoft stack but is part of an increasing focus by Microsoft to assist businesses with increasing their security posture in a world where threats are becoming more sophisticated and the likelihood of zero-day threats are increasing.
The inclusion of both Microsoft Defender for Endpoint and Microsoft Defender for Office 365 under a single, easy to consume Microsoft 365 Business Premium license may make this the go-to choice for businesses, but it would be prudent to also consider third party alternatives to created siloed instances of the internal environment and the security console. The continued growth of cloud based services under the Microsoft Azure platform and the ability to manage these assets from one place must also be a strong factor in the decision of what security products to use.
This is where a number of third party applications can also be considered which now only tap into existing Microsoft tenancies but also with their extensive exposure to this landscape for a considerable time period, can be seen as suitable alternatives to endpoint protection. Through API’s with third party applications the ability to connect environments into one another is becoming simpler, ensuring that businesses have an arch of different security products available to them to protect their business. T should be noted though that any 3rd party integration is unlikely to have the level of feature integration that the Microsoft Security suite now called Defender would give.











